A.
- State one example of a peripheral that might be attached to a personal computer (PC), but not always.
- Outline 2 significant purposes of a network.
- Describe one advantage of using a PC in stand-alone mode, not attached to a network.
- Outline what the term human resources means in a computer system.
- Explain why computer systems require both hardware and software.
B. Assume that a student is searching for news articles about automobile manufacturing in China.
The student is using a wireless connection at a school.
- Describe what the term client refers to in this situation.
- Explain the purpose of a DNS server during this scenario.
- Outline 2 different places that contain routers that are being used by the student.
- Explain how a firewall might provide a use service in this situation.
- Describe the role of a web-server in this situation.
C.
- Describe a situation when new software developments would be a disadvantage for an Internet user.
- Explain the ethical responsibilities of the software industry regarding benefiting and disadvantaging Internet users.
D. Imagine that a new automated online ticketing system is being developed for people who wish to reserve and purchase airline tickets.
- Outline 3 different groups of stakeholders for this system.
- Describe 2 ways that needs and wishes can be collected before this system is designed.
- Describe 2 hardware issues that must be considered when designing this system.
- Describe how end-users can be involved in testing and debugging the software for this system.
E. Assume that a school wishes to install a set of networked printers, enabling teachers and students to print documents in color and/or black and white. The school already has a LAN, and wishes to add 10-20 new printers.
- Describe how current systems could be studied during the analysis phase.
- Describe how literature searches might be helpful during the analysis and design phases.
- Outline some organizational capabilities that should be considered during the design phase.
- Assume that the school wishes to allow printing from teachers’ PCs that are attached to the school’s LAN, as well as printing from laptops that are using the schools WIFI network. Draw a data-flow-diagram showing how the most important components interact with each other.
F.
- Outline 2 advantages of constructing a prototype before writing a computer program.
- Explain why software development is usually an iterative process.
- Explain two possible undesirable consequences of not involving the end-user
in the design process.
G. Assume that a school will purchase a new computer system that is used to help students apply to universities. It helps the counselors keep track of which students have completed various stages in the application process. It also includes communication software that can transmit information like transcripts and teacher recommendations from the school to a university.
- Explain two reasons why security is a significant issue in this system.
- Outline two ethical issues connected to user training and/or lack of user training.
- Outline two usability issues that the school should consider before
choosing a new system.
H.
- Define the term usability.
- Explain the importance of learn-ability as it relates to usability.
- Outline two common usability issues connected to cell-phones – do NOT include issues connected to any specific disabilities like old age or lack of hands. You must discuss usability problems that “normal” people experience.
- Explain two significant differences between electronic digital devices and other electrical devices that are NOT digital. Examples would help significantly here. Outline two accessibility features that would be appropriate to improve the usability of a personal computer for a user who has only one hand. Outline two usability problems that have prevented voice recognition systems from becoming more widespread in the computer industry.
I. Google is trying to market a self-driving car. This would be particularly useful for blind people who wish to have their own car and enjoy the freedom and mobility that it provides.
- Outline 3 sets of stakeholders for the Google Car System.
- Describe 2 ethical issues associated with this system.
- Describe 2 economic issues associated with the Google Car System.
====
1. Identify two installation processes for a new system. [2 marks]
2. Explain how data is exchanged between RAM, the CPU, and cache memory. [2 marks]
3. Describe how a number in base n would be converted to decimal. [2 marks]
4.
(a) Convert the decimal number 72 to binary. [1 mark]
(b) Convert the binary number 01011100 to hexadecimal (base 16). [1 mark]
5. Describe two types of data that would be used when testing an application. [2 marks]
6. Outline a software solution that can reduce the amount of time required [2 marks]
to transmit data in a Wide Area Network.
7. Explain what pseudo-code is and when it is used. [2 marks]
8. Outline one advantage of creating a prototype before designing a computer [2 marks]
system.
9. Explain the rationale for first introducing a cache to CPU architectures, [2 marks]
and the resulting benefit from utilizing a cache.
#10
The GOOD STUFF company has a web-site, where anybody can place orders for products.
To place an order, the customer must:
– choose a product
– enter customer name
– enter customer’s address
– enter a credit card number
The order is then printed on paper and sent to a warehouse, where the products are packaged and delivered. Orders are shipped without any verification.
(a) Outline how data validation might be used during the ordering process. [1 mark]
(b) Explain the difference between data validation and data verification. [2 marks]
(c) Outline how the web-server can securely store the user’s private data,
preventing GOOD STUFF employees from stealing and misusing bank information. [2 marks]
The GOOD STUFF company would like to build a more ambitious version of the website which, among other features, will better facilitate cooperation with their business partners.
(d) Identify the relevant stakeholders when planning the new system. [2 marks]
(e) Explain the possible consequences of failing to involve the end-user in the [3 marks]
design process.
#11
(a) Outline how a Bubble Sort algorithm functions. [2 marks]
(b) Assume that a Bubble Sort algorithm requires 10 seconds to sort an array [2 marks]
containing 2 million numbers.
State approximately how long the same algorithm would require to sort 8 million numbers.
(c) Using pseudocode, construct an algorithm that finds the LARGEST value [4 marks]
in an array that contains 1 million numbers. Assume that the numbers are already stored in an array named DATA. The numbers in the array are in random order.
(d) Describe two ways to perform a search on the data in part (c). [2 marks]
#12
A college occupies a building on three levels. A computer network, using wires, is in place but needs to be extended. It is suggested that the current system be replaced by a wireless network which provides connection to a file server and offers support for off-campus staff who need to access network resources.
(a) Describe how communication over the network is broken down into different [3 marks]
layers.
(b) State a network technology that could provide secure access to the remote staff. [1 mark]
(c) Outline the advantages and disadvantages of wireless networking. [4 marks]
(d) Describe two methods for making the network secure. [2 marks]
#13
The flowchart below represents an algorithm that displays a sequence of numbers.
The word “even” means that a number is evenly divisible by 2.
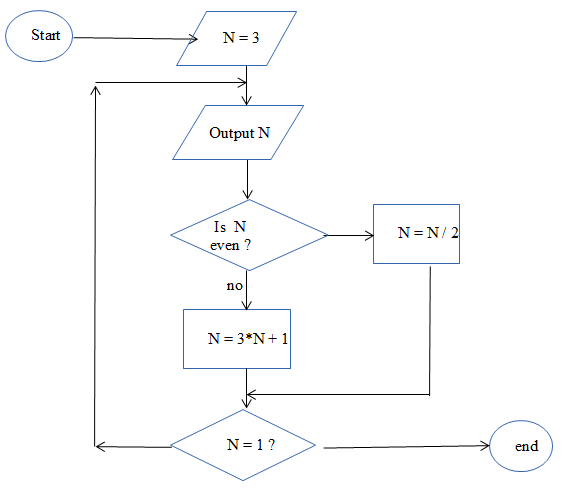
(a) Read the algorithm and state the sequence of numbers that it produces. [4 marks]
(b) Construct an algorithm using pseudo-code that sums the following numbers. [6 marks]
2 + 4 + 8 + 16 + 32 + 64 + …. + 65536
#14
(a) Define linked-list. [2 marks]
(b) Explain the steps needed to add a node to a linked list. [4 marks]
Use diagrams to show adding a note at front, middle, and end.
(c) Explain the steps needed to remove a node to a linked list. [4 marks]
Use diagrams to show removing a note from front, middle, and end.
(d) Explain what is meant by a circular linked list. [2 marks]
#15
There are many possible ways to store a list of data in a computer. One possibility is to use an array. Another possibility is to use a collection. An array is a static data structure, whereas a collection is a dynamic data structure.
(a) Explain the major difference between static and dynamic data structures. [2 marks]
A stack is a list with specific access methods:
– push(DATA) is used to put a value into a stack
– pop() is used to remove an item from a stack
Study the following algorithm.
// Assume INFO is a stack that is empty
// Assume NAMES is an array containing 5 names
NAMES = [“Al”,”Betty”,”Carl”,”Deb”,”Ed”]
loop C from 0 to 4
DATA = NAMES[C]
INFO.push(DATA)
end loop
loop while not INFO.isEmpty()
DATA = INFO.pop()
output DATA
end loop
(b) State what will be displayed by the algorithm above. [3 marks]
(c) Explain the essential differences between a stack and a queue. [2 marks]
The diagram below shows a Linked-List, with appropriate pointers.
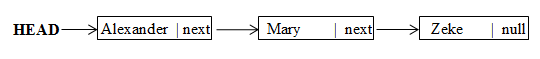
(d) Explain the meaning of “null” in the diagram above. [1 mark]
(e) Explain what would be accomplished by the following command:
HEAD = HEAD.next [2 marks]
#16
Computational thinking involves using the capabilities of one’s (human) brain and the capabilities of computer ‘brains’ to represent and solve problems and accomplish tasks.
Discuss five aspects of computational thinking. [10 marks]
#17
Below is a balanced binary search tree.
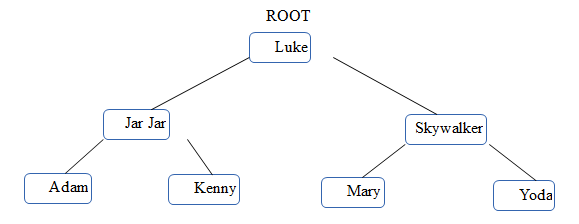
(a) State what would be printed by a PRE-ORDER traversal of this tree. [2 marks]
(b) Explain where a new node containing “Louise” would be added to this tree. [1 mark]
(c) Explain why deleting a node from a binary-search tree could be significantly more complex than adding a new node. [2 marks]
(d) Draw a binary tree which correctly represents this formula:
(a + b) / (c – d*e ) [3 marks]
(e) Look at your answer to (d). State what would be printed by a POST-ORDER traversal of the formula tree. [2 marks]
Paper 3 (CGI) HL ONLY
Pacific FX is working on “a computer game to be played on ordinary home computers and a short animated commercial.”
(1)
Explain the difference between “rendering in real time” and “completely prepared offline”, including specific reference to which method applies to which one of the products.
[4 marks]
(2)
Explain what “keyframes” are. [2 marks]
(3)
Explain what the “uncanny valley effect” is, including a specific example of where this might be a significant issue, with specific reference to video games and/or animated commericals. [3 marks]
(4)
On p. 5 it says “because scanline rendering is an embarrassingly parallel algorithm it is particularly suited to be processed by GPUs.” Explain what the term “embarassingly parallel algorithm” means, including a specific example of how this could be useful in a GPU. [3 marks]
(5)
(a) Explain what the term “motion capture” means. [3 marks]
(b) Explain why “motion capture” is less useful in a video game than when making a movie.
[2 marks]
(6)
(a) Explain what “rendering farms” are. [2 marks]
(b) Discuss whether “rendering farms” are more useful in video game production or more useful for creating a short animated commercial. [3 marks]
(7)
In the Animation Production Pipeline, some tasks can be performed simultaneously with some other tasks, while some tasks must be completed before other tasks start.
Choose one task than can be performed simultaneously with another task, but which must be completed before another task. In each case, explain why this is the case. [4 marks]
(8)
“Pacific FX has employed some computer science graduates who are currently undergoing training. Xiao-Ling explained that as part of this training course they look in detail at various ethical considerations that a responsible company should take into account when developing their CGI projects.”
The 12-mark question will be based on the challenges faced. Here are some of the questions (I found on the Internet) on what you could be asked.
To prepare a report on the different animation algorithm currently being used and how they might change in the future
- What are the current animation algorithms?
- What is scan-line rendering algorithm?
- What is ray-tracing algorithm?
- Investigate the techniques of motion capture as a viable option for their commercial project
- Investigate the demands made by the various processes and algorithms available.
- Prepare the ethics module for the training course.
- Incorporate new techniques as they arise.
- Why should they need to change current algorithm? What is driving this need for change?
- How will changes to algorithm meet this need? What will the changes be?
- What are the countermeasures and why do they work?
- “Xiao-Ling and Pacifi c FX’s challenges for the immediate future are to investigate the demands made by the various processes and algorithms available”. (Page 5) Explain in details scanline rendering and ray-tracing algorithms for use in the computer game project.
- “Pacific FX has employed some computer science graduates who are currently undergoing training. Xiao-Ling explained that as part of this training course they look in detail at various ethical considerations that a responsible company should take into account when developing their CGI projects.” Ignoring financial issues, discuss one ethical issue that requires specific care and consideration when creating a short animated commercial.
